About Dark Vortex
Dark Vortex, earlier known as scriptdotsh.com from 2018 to 2019 started off as an offensive security blogging site, until late 2020 when Chetan decided to release Brute Ratel Command and Control Center and started providing Security Training Programs.
Contact
For any enquiries on training services or other queries, reach us at paranoidninja@0xdarkvortex.dev
For Brute Ratel support, reach us at chetan@bruteratel.com
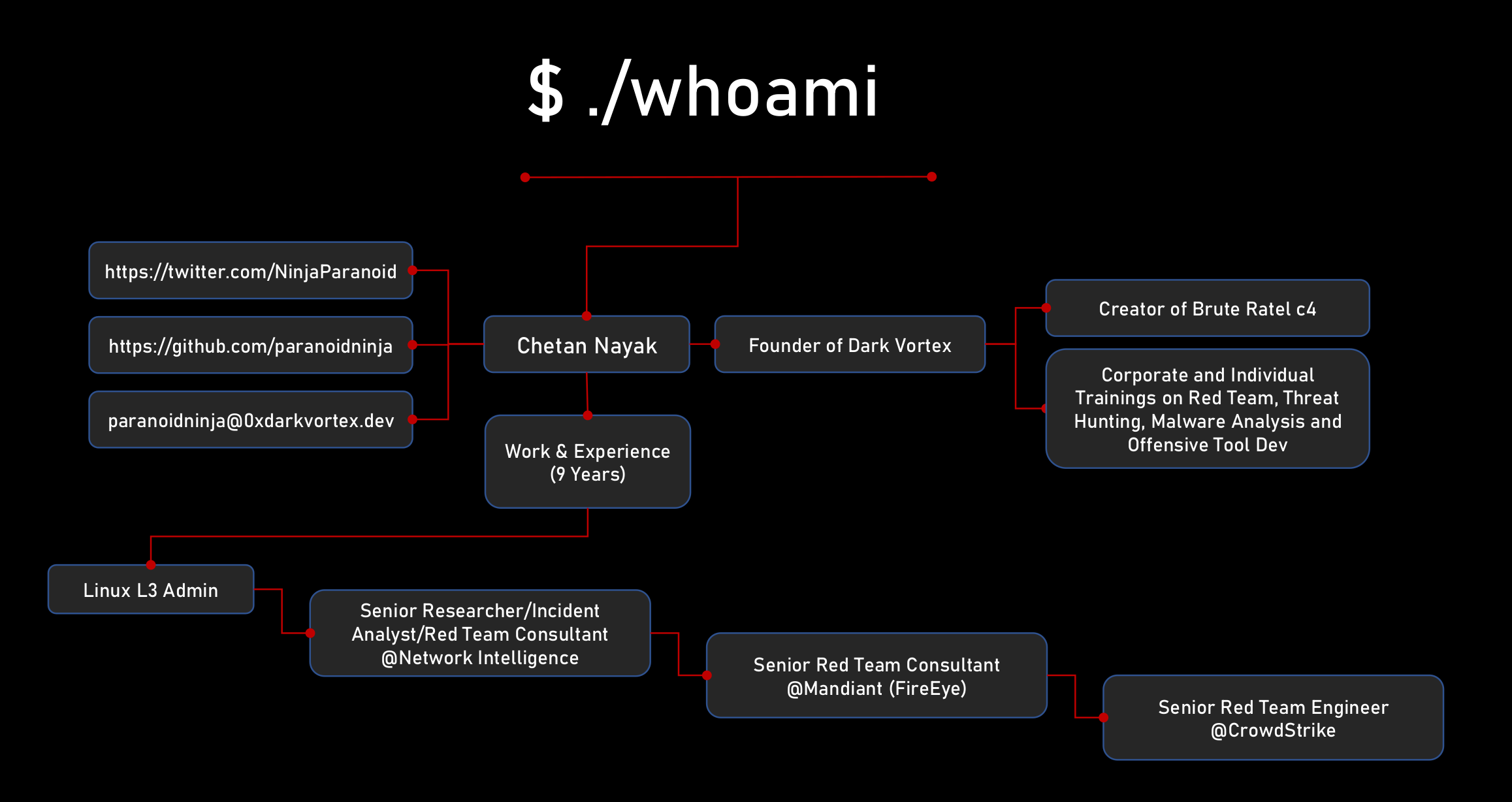
About Chetan Nayak
Chetan Nayak has 12+ years of experience in Information Security. He started his career as a Linux Engineer where he learn’t how to automate several operational tasks via various programming languages. After serving 3 years as a Linux L3 Systems Engineer, Chetan provided trainings as a freelancer on Cyber Security and the Secure Programming with C and Assembly.
He later joined Network Intelligence in 2016 as a Senior Researcher and Developer in the Research & Development divison. Here, he built an EDR platform which utilised Elastic, Logstack and Kibana (ELK) stack, Big Data Analytics alongside a Kernel Mode Device Driver and a Userland Service for windows API hooking. In early 2018, Chetan moved to the Threat Hunting division where he tracked several threat actors while responding to incidents. Later that year, he joined the offensive side of security where he performed Red Team engagements including but not limited to phishing, physical breach and a lot of payload development.
In early 2019, Chetan joined the Mandiant division of FireEye as a Senior Red Team Consultant. He performed several Red Team engagements, Pentests and Adversary Simulation. He also performed a few cases of Incident Response till late 2020.
Chetan quit Mandiant in 2020 in the pursuit of building his own Command and Control Center Brute Ratel. With the extensive knowledge and experience that Chetan gained over time, he built an extremely advanced pluggable C2 which became more powerful with every release. He released Brute Ratel in December 2020 before joining CrowdStrike as a Senior Red Team/Detection Engineer. Here, he was tasked with finding detection gaps for the Falcon EDR, executing MITRE evals for various threat actors along with assisting the Red Team for offsec tooling. Alongside working in Crowdstrike, Chetan also started providing various offensive training workshops via his venture Dark Vortex.
Chetan quit Crowdstrike in January 2022 to pursue fulltime Brute Ratel development and Training Workshops.
Programming Languages Experience: C, C++, ASM (x86/x64), Golang, Python3/2.7, Ruby, Java, Haskell, Rust, PowerShell, C#
You can follow his tweets at @NinjaParanoid on Twitter.