Offensive Tool Development
LIVE WORKSHOP IS NOW AVAILABLE
AS A VIDEO COURSE FOR CUSTOMERS
What To Expect
The Offensive Tool Development is the first course which is dedicated to Windows API exploitation to build your own tools for Red Team Engagements. If you have completed the Malware On Steroids course, then you can merge the capabilities you build during this course with the Command & Control built during the MOS course. This helps you to build your own CnC modules, all of which can be run in memory for detection evasion. There are a lot of courses which focus on exploitation, reversing and other offensive stuff, but none of them focus on writing your own tools and brining your own toolkit during an engagement.
This course is highly technical in nature, involving a lot of coding and all the tools will be written in either C or C++, sometimes PowerShell (maybe 5%) to make sure the user has capabilitiy to load every tool in memory and evade memory artefacts or detections. During the course, you will build your own reflective tools and shellcode for Host Enumeration, Lateral Movement, Domain Enumeration and Domain Privilege Escalation. You will learn to build different types of remote access tools running over different protocols including RPC, SMB, and HTTP and use exploit Windows Security Tokens for lateral movement within a Domain Environment.
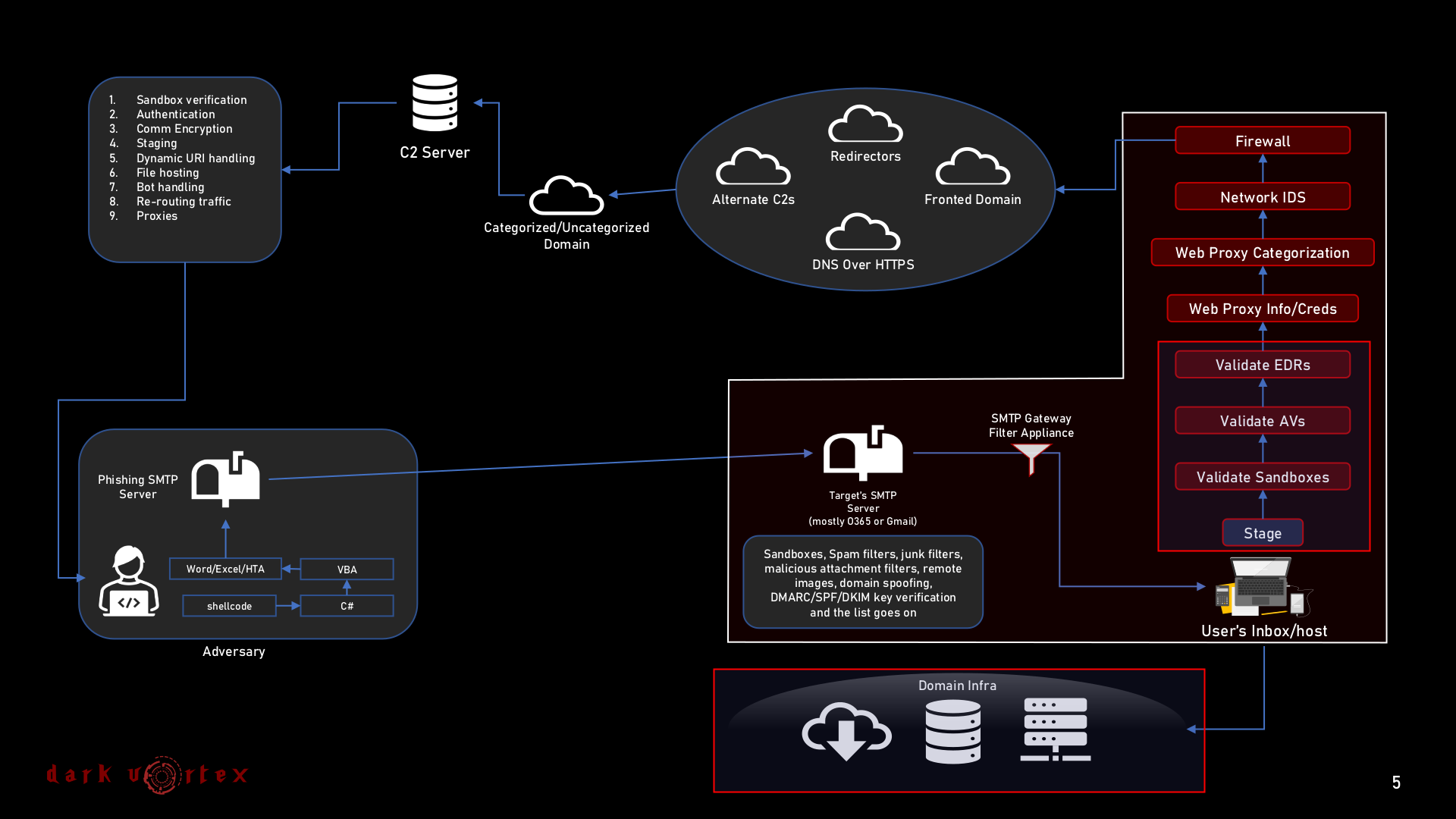
The below figure highlights a brief overview on the focus area of the training session.
Training Content
The total course duration are 4 days Online Interactive training sessions over Google Meet. Virtual environments such as Active Directory Lab/C2 access/Domain access will be provided where necessary. A detailed information on the training content can be found here.
Certification
Dark Vortex provides Certificate Of Completion for every completed course. This certificate may be verified by contacting paranoidninja@0xdarkvortex.dev using the enrolment ID from the given certificate.
Prerequisites
The course is highly practical in nature and involves a lot of programming in C/C++, reverse engineering in windbg/x64dbg. Its important to have a good grasp of the below fundamentals before approaching the course.
- Basic Understanding of operating system architecture
- Basic Understanding of the Windows Active Directory environment
- Fundamental knowledge of programming with C/C++
- Familiarity with programming concepts (pointers, referenceses, addresses, data structures, threads, processes)
- Strong will to learn and creative mindset.
System Requirements
During the course, we will be working with different virtual machines which will involve cloning, creating, and snapshots and several other hands-on exercises. A properly configured system is extremely important to fully utilize the benefits of the training session. We strongly request you to have fully configured system which meets the below requirements for the course. All the requirements mentioned below are either freely available or open source.
- Windows 10 (Virtual Machine)
- A laptop with atleast 16GB RAM to support 2 VMs running at the same time.
- VMware/VirtualBox installed
- Good Internet Connectivity
- Visual Studio with C/C++/C# packages installed
- Visual Code/Editor of your choice
- x64dbg
- CFF Explorer
- Sysinternals Tookit
- Process Hacker
- Kali Linux/Ubuntu 20.04 (Virtual Machine)
- VS Code
- Mingw-w64
- Nasm
- Wireshark
NOTE: Make sure you have a snapshot of each virtual machine before you start the class, just in case you have to revert everything back to stock if your Virtual Machine crashes during the training.
Course Fees
Offensive Tool Development | 4 days (Interactive/Online)
At the end of the course, you will receive a Certificate of Completion and all the training materials including course PDFs/slides, content materials, source code for tools built during your training sessions.
$2000 USD
*Inclusive of taxes and certification
We conduct live training sessions which are conducted remotely and do not contain pre-recorded videos. For enquiries on training programs or other services, reach us at paranoidninja@0xdarkvortex.dev